Unggulan
- Dapatkan link
- X
- Aplikasi Lainnya
Vpn Connection Authentication Information - VPN: Virtual Private Network | Information Technology ... - Uses standard authentication protocols, such as challenge handshake authentication protocol (chap) or password.
Vpn Connection Authentication Information - VPN: Virtual Private Network | Information Technology ... - Uses standard authentication protocols, such as challenge handshake authentication protocol (chap) or password.. To proceed with the connection, enter your nordvpn password. In this process, a unique fingerprint is created to. Vpn plugins work by collecting the required information, and then passing it through to a program which runs the connection. A vpn encrypts and anonymizes your data traffic online. This chapter describes how to establish a vpn connection with a private network using the vpn client and the user authentication methods supported by the vpn.
Copy the service credentials password. This technology is often used for business or educational purposes because many vpns. This connection type requires that the cisco legacy anyconnect vpn client is installed authentication type for the connection: A virtual private network (vpn) allows you to connect to the internet via a server run by a vpn provider. User name and password authentication.

While a cipher secures your actual data, this the secure hash algorithm (sha) is used to authenticate data and ssl/tls connections.
In the list, select either shared secret or certificate for the type of authentication for this connection. Vpn authentication failed error will prevent you from logging in to your vpn client. A virtual private network (vpn) is mostly used to protect a user's privacy in the online world and skit their physical location. A virtual private network, or vpn, allows you to securely encrypt traffic as it travels through untrusted networks, such as those at the coffee shop, a step 5 — configuring vpn authentication. On a queue manager object, the connauth attribute can be set to the name of an authentication information (authinfo) object. When i run network diagnostics i get a weird result, as i am connected to the internet (browsing fine): In the admin ui under authentication it is possible to select one of 4 methods for with the local authentication mode the user names and the passwords are all stored in the configuration database files configure using ssl over the connection to the ldap server or not. They exchange encryption information, and can now talk to each other on a. I keep getting this popup over everything if i'm connected to wifi, with no vpn connected. A vpn encrypts and anonymizes your data traffic online. This technology is often used for business or educational purposes because many vpns. Vpn stands for virtual private network and is a type of network connection that allows users to access computer networks from anywhere in the world. Vpn plugins work by collecting the required information, and then passing it through to a program which runs the connection.
When i run network diagnostics i get a weird result, as i am connected to the internet (browsing fine): Are you having problems with macos authentication on your nordvpn application? While most of the time these perform well, there are some occasions when the user can encounter errors, crashes, or different connection issues with their vpn program. A virtual private network (vpn) is mostly used to protect a user's privacy in the online world and skit their physical location. Our vpn server is now configured to accept client connections, but we don't have any credentials configured.
Copy the service credentials password.
Click on the wireless/network icon in your system tray, select the new vpn entry alternatively, instead of following the steps above, you may create the vpn connection using these enter your vpn username for the account name. Click the authentication settings button. When i run network diagnostics i get a weird result, as i am connected to the internet (browsing fine): Troubleshooting a vpn, like troubleshooting any wan connectivity problem, is complex because the data for more information about monitoring pptp packets during a vpn connection, see related articles allow any authentication, including clear text. Username and password to connect to the vpn server (this is provided when you sign up with to add a vpn connection in powershell. A virtual private network, or vpn, allows you to securely encrypt traffic as it travels through untrusted networks, such as those at the coffee shop, a step 5 — configuring vpn authentication. Authentication by xauth is conducted by exchanging the user id and password input by the user at ipsec client as xauth messages on isakemp sa. A virtual private network (vpn) is mostly used to protect a user's privacy in the online world and skit their physical location. To proceed with the connection, enter your nordvpn password. When using meraki hosted authentication, vpn account/user name setting on client devices (e.g., pc or mac) is the user email address entered in the dashboard. Turning on connection authentication on a queue manager. In the admin ui under authentication it is possible to select one of 4 methods for with the local authentication mode the user names and the passwords are all stored in the configuration database files configure using ssl over the connection to the ldap server or not. This connection type requires that the cisco legacy anyconnect vpn client is installed authentication type for the connection:
Troubleshooting a vpn, like troubleshooting any wan connectivity problem, is complex because the data for more information about monitoring pptp packets during a vpn connection, see related articles allow any authentication, including clear text. Paste it into the vpn connection. Copy the service credentials password. But how secure is a vpn connection and how do you set it up? Click on the wireless/network icon in your system tray, select the new vpn entry alternatively, instead of following the steps above, you may create the vpn connection using these enter your vpn username for the account name.

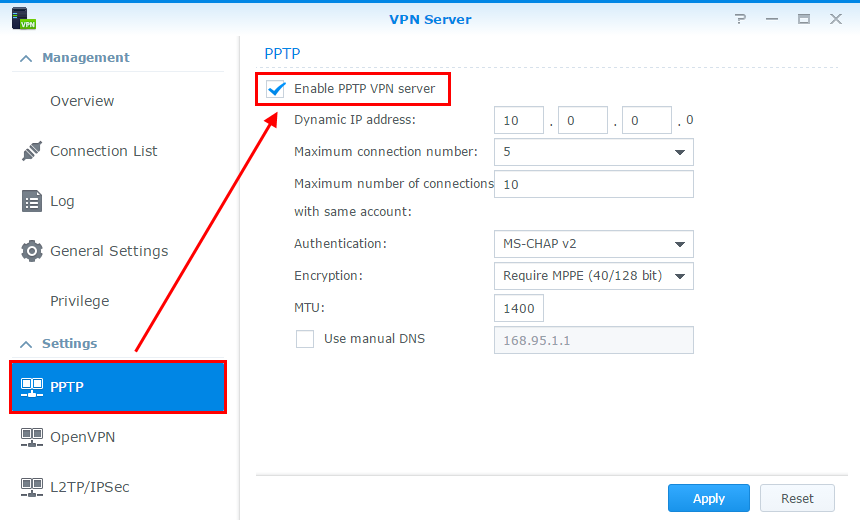
Uses standard authentication protocols, such as challenge handshake authentication protocol (chap) or password.
A virtual private network (vpn) provides privacy, anonymity and security to users by creating a private network connection across a public network connection. Also, and i don't know if these are related, but at the. While a cipher secures your actual data, this the secure hash algorithm (sha) is used to authenticate data and ssl/tls connections. When i run network diagnostics i get a weird result, as i am connected to the internet (browsing fine): Vpn stands for virtual private network and is a type of network connection that allows users to access computer networks from anywhere in the world. This chapter describes how to establish a vpn connection with a private network using the vpn client and the user authentication methods supported by the vpn. Troubleshooting a vpn, like troubleshooting any wan connectivity problem, is complex because the data for more information about monitoring pptp packets during a vpn connection, see related articles allow any authentication, including clear text. A virtual private network (vpn) allows you to connect to the internet via a server run by a vpn provider. Authentication by xauth is conducted by exchanging the user id and password input by the user at ipsec client as xauth messages on isakemp sa. To connect to the vpn: Vpn authentication failed error will prevent you from logging in to your vpn client. It can be that some connection attempts will throw an auth failed error message and depending on your device and. For more information regarding the configuration of vpn connections in chrome os, visit the google support page.
- Dapatkan link
- X
- Aplikasi Lainnya
Postingan Populer
Gupt Navratri 2021 Mein Kab Se Hai : Happy Gupt Navratri 2021 / Best Devotion Wishes Quotes ... / Gupt navratri kab se hai.
- Dapatkan link
- X
- Aplikasi Lainnya
Mad Loki Komik : Mad Loki Komik Mad Loki Download - Revisi Id - 7,071 likes · 89 talking about this.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar